How to source and close new logo accounts with partners
PartnerTap
JULY 11, 2023
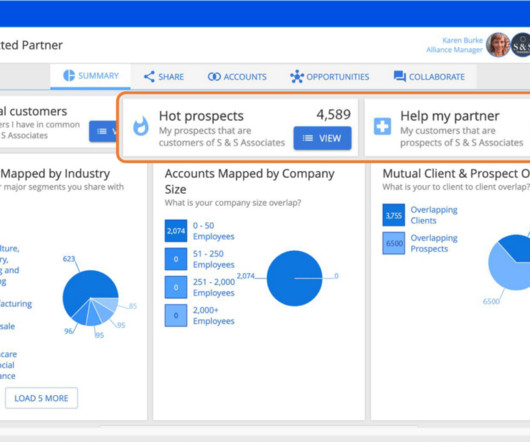
Sourcing new logo accounts is a top priority for every enterprise partnership. Unfortunately, the bulk of those meetings end up being spent identifying which accounts to target. Step 2: Source new logo accounts in one-click How many times has your team spent a month manually mapping partner accounts you received in a spreadsheet?


































Let's personalize your content